We’ve developed an investigative process that mirrors the work of a seasoned detective, designed to uncover criminal activity while safeguarding privacy and legal rights. Imagine a team of digital detectives, each with a specific crime specialty, working together to follow clues and build a solid case.
Our process begins with the SAL model, a human behavioral model that drives the Unique ID Reconciler. Together, they serve as the first line of investigation. The SAL model analyzes behaviors within vast datasets to separate normal records from those that are suspicious, while the Unique ID Reconciler ensures that each flagged record is accurately identified. This combination allows us to use minimally invasive data, ensuring that we only focus on records that truly warrant further investigation.
Once potential anomalies are identified, our specialized Digital Detectives take over. Each detective is an expert in a particular type of crime, focusing their efforts on the suspicious records identified earlier. They don’t stray from the path—they dig into the flagged data to uncover deeper connections, ensuring the investigation is precise and relevant.
Guiding these detectives is the NDSI network—the neighborhood where all clues are found. But this isn’t just any neighborhood; it’s made up exclusively of data from government and commercial entities. The Network-Sequencing-Chains operate within this network, creating a map for the detectives to follow. It’s like canvassing an entire neighborhood, but on a much larger scale, and with only the most relevant data sources at hand. Our Digital Detectives work not just on single cases, but in mass by scenario, allowing them to address complex criminal patterns across broader contexts.
As the Digital Detectives gather clues from the NDSI neighborhood, they piece together a comprehensive case. The Network-Sequencing-Chains ensure that every step is connected, every clue is relevant, and nothing unnecessary is included.
Finally, the detectives compile their findings into a detailed report, complete with a confidence rating. The confidence rating is a crucial component of the report—it quantifies the strength and reliability of the gathered evidence. This rating helps law enforcement and government personnel quickly assess how much weight to give the report and determine the urgency of the case. A higher confidence rating indicates that the evidence is robust, and the findings are likely accurate. This structured, clear assessment makes it easier for human investigators to prioritize while taking swift and informed action.
After the report has been successfully transmitted to the appropriate law enforcement or government personnel, WGDS takes the additional step of purging the records from our system. This final safeguard ensures that once our job is done, no unnecessary data is retained, maintaining the highest standards of privacy and security. By securely deleting the data, we protect all parties involved, respecting both legal and proprietary boundaries.

By digitalizing criminal investigations at scale, we are replacing traditional manual methods with a groundbreaking human-machine teaming model. This innovative approach harnesses the power of advanced AI and machine learning to work alongside human expertise, vastly improving the speed and precision of identifying and prosecuting traffickers.
The beauty of human-machine teaming lies in its ability to combine the strengths of both entities. Machines excel at processing vast amounts of data with incredible speed and accuracy, identifying key indicators that might be overlooked by human investigators. On the other hand, humans bring critical thinking, contextual understanding, and ethical considerations to the table, ensuring that the insights generated by machines are actionable and grounded in reality.
For instance, the Network-Sequencing-Chains within WGDS’s system guide Digital Detectives through a meticulous investigative process, much like a real-world canvas but executed with lightning speed and precision. These chains ensure that each step in the investigation is legally compliant and minimally invasive, collecting data evidence efficiently and effectively. The result is a comprehensive intelligence report that includes a confidence rating, supporting data evidence, and potential locations, providing stakeholders with the information they need to take swift and decisive action.
Our system integrates diverse data sources, automates the analysis of vast amounts of information, and guides investigators through a structured, legally compliant process. Our specialized network by WGDS is a specialized mosaic data lake designed for combating human trafficking. It integrates diverse data sources, ensuring secure and confidential data handling while allowing passive monitoring of supply chains and customer data.
The specialized network provides real-time access to pre-defined data, streamlining the investigative process. This network is vital for gathering data evidence quickly and accurately, significantly enhancing the efficiency of human-machine teaming.
By leveraging our network, investigators gain immediate insights, reducing time and resources needed to identify trafficking activities. This network is crucial for rapid, effective interventions, making a substantial impact in the fight against human trafficking.

At WestGate Data Science, our team combines decades of experience across various sectors, including technology, public service, and organizational behavior. We have a proven track record in integrating complex data systems, developing advanced algorithms, and leading large-scale projects for major corporations, healthcare systems, and government agencies.
Our collective expertise enables us to create innovative solutions that leverage cutting-edge technologies such as IBM’s mainframe, data fabric, and hybrid cloud environments. We excel in data analysis, system integration, and digital transformation, ensuring our Digital Detective system is both efficient and secure.
Our diverse backgrounds in public safety, city governance, financial institutions, and technology innovation provide a comprehensive understanding of the practical applications and strategic implementation of our solutions. Together, we are dedicated to revolutionizing the fight against human trafficking by developing a robust, autonomous system capable of identifying traffickers and victims on a massive scale. Key to this effort is our use of data evidence chains, which link critical data points to build comprehensive case pictures, aiding detectives and investigators in tracing connections, verifying accuracy, and building strong cases against traffickers
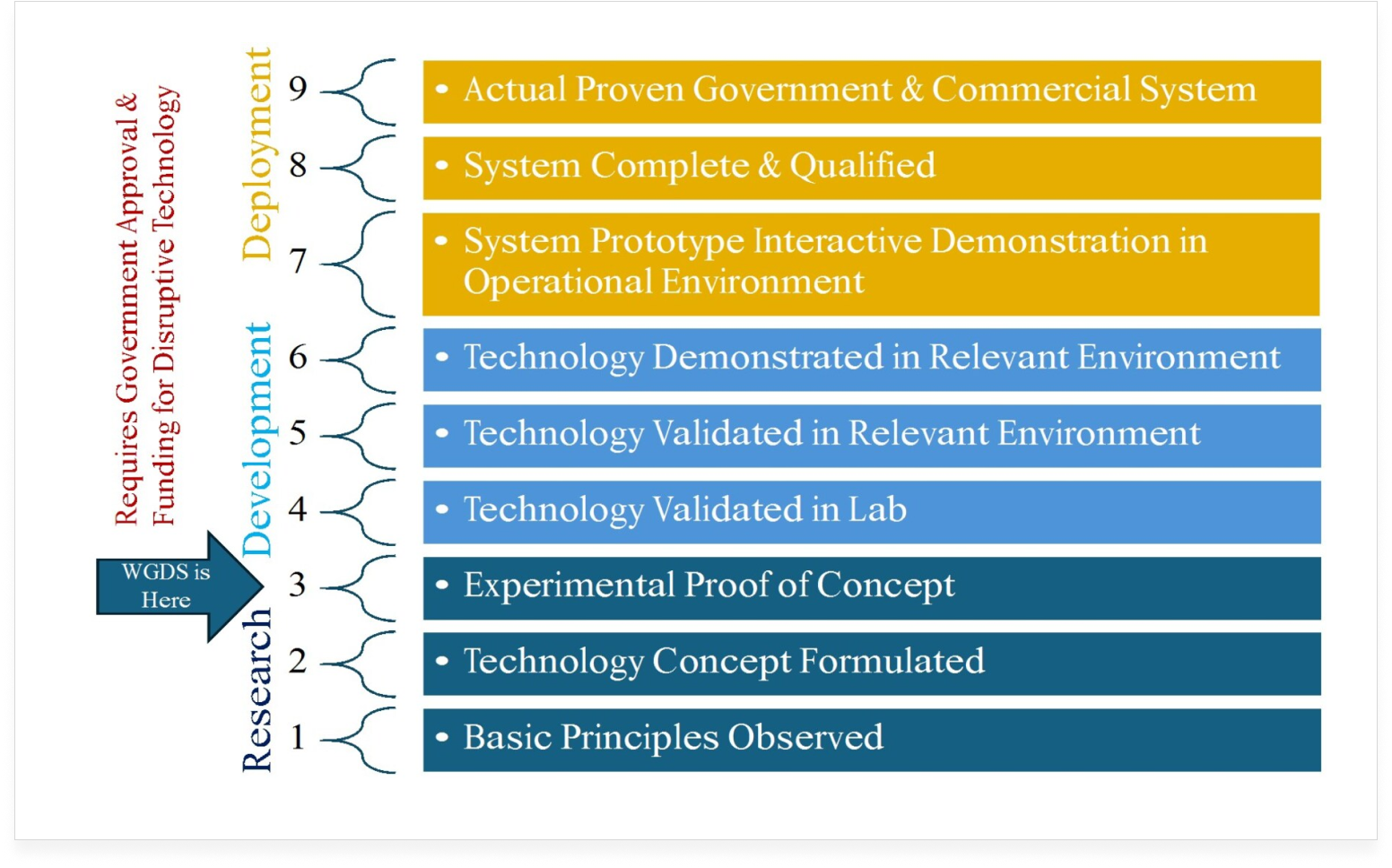
Ensuring the quality and accuracy of our Digital Detective system is a foundational priority as we develop this innovative technology. Our approach integrates rigorous data validation and continuous improvement processes to uphold the highest standards from the outset.
During the development phase, our team employs advanced data analysis techniques and machine learning algorithms to cross-verify information from multiple sources. By leveraging diverse datasets, we aim to identify and correct discrepancies, ensuring that our system’s outputs are reliable and precise. This multi-layered verification process is designed to enhance the accuracy of our trafficking detection capabilities.
We are committed to ongoing monitoring and auditing of our system’s performance even in its developmental stages. Regular updates and refinements to our algorithms are planned to keep them effective against evolving trafficking patterns. Additionally, feedback loops will be established to incorporate new data and insights, continuously improving our system’s detection capabilities.
© Copyright 2024 WestGate Data Science. All rights reserved
Follow :